Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
7 Cybersecurity Tips for Your Team
7 Cybersecurity Tips for Your Team
Helpful Cybersecurity Tips from our Nerds
The global pandemic has prompted your office to work from home, or your team is back to the office? Since the epidemic started, and most people had to work remotely, there has been a rise in cyber-attacks worldwide. The FBI reported an 800% increase in cybercrimes. From 1000 daily complaints, it jumped to 3,000 to 4,000 complaints. That is why learning the best ways to protect you and your company’s data is so critical nowadays and working with cybersecurity professionals is more critical than ever.
Cybersecurity needs to be everyone’s priority, but it is not everyone’s strength. That is why we came up with 7 cybersecurity tips that your team needs to know and practice.
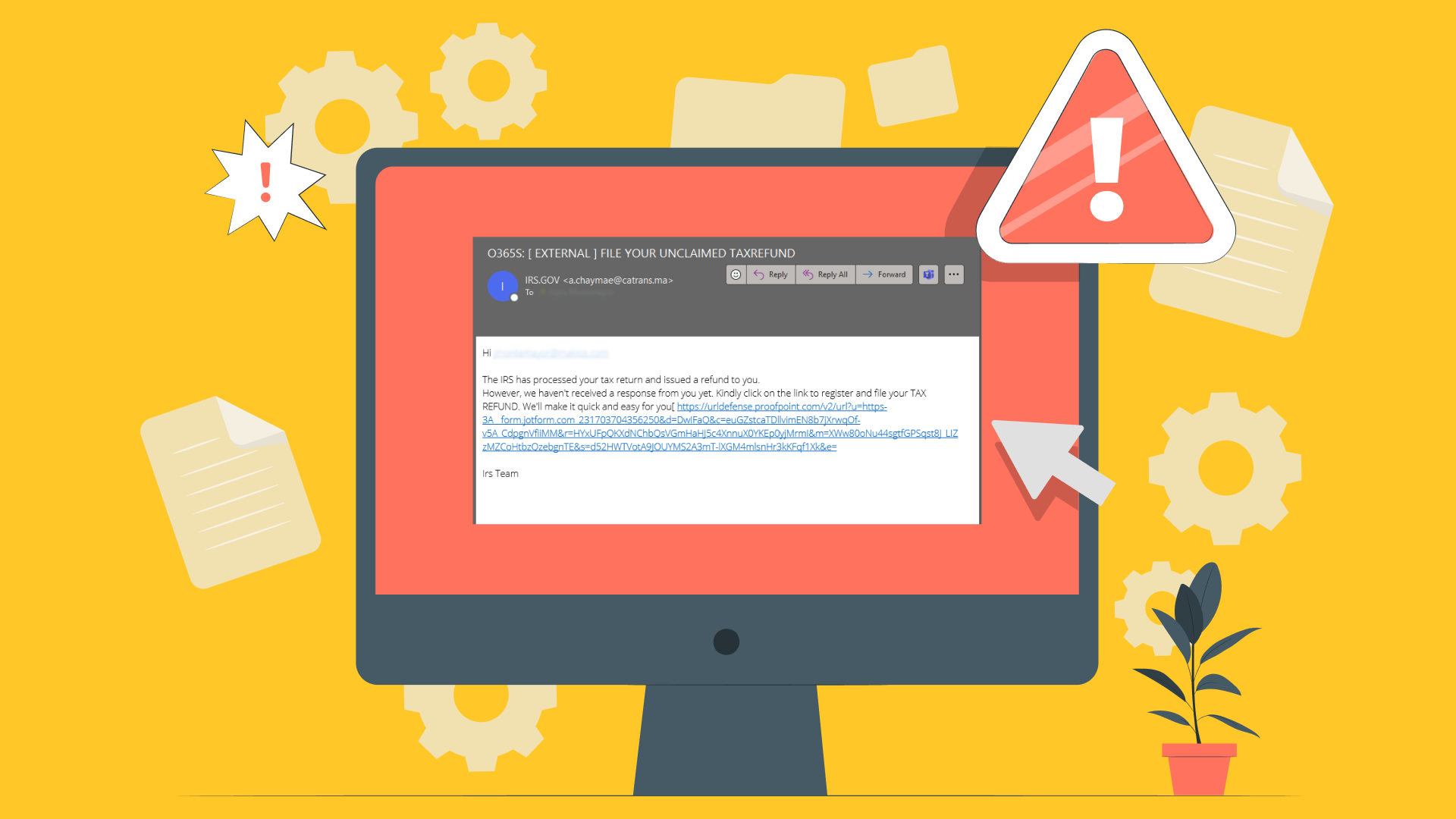
1. Watch for suspicious emails
Phishing attacks are rising to a level with over 60,000 phishing sites reported in March alone, according to APWG’s Phishing Activity Trends Report for Q1 2020. A phishing email is a scam from an unsecured source pretending to be a trusted individual, such as known or unknown companies or even a CEO.
Signs that an email is fraudulent include invalid email addresses, bad grammar, a sense of urgency, strange requests, or unknown hyperlinks or unexpected files.
Here are a few helpful questions to ask yourself before clicking or responding:
- Is the offer too good to be true?
- Are you expecting the message?
- Is the sender someone you often interact with?
- Are links in the message looking legit but pointing somewhere else?
2. Use VPN working remotely
Working remotely, you can help protect your organization data by using a VPN if your company has one. Public Wi-Fi networks can be risky and make your data susceptible to being intercepted.
A Virtual Private Network is a private network that encrypts data and hides your IP address to protect the user. That means that your team will have a private and secure connection with your office while working remotely.
You can access a VPN on your laptop or mobile phone, which is essential when working remotely.
3. Change passwords regularly
According to the Verizon Data Breach Investigations Report, compromised passwords are to blame for 81% of hacking-related breaches. Reusing passwords and not updating them at least every 90 days makes it easy for hackers to breach your business accounts.
Set up timers on login-required software that forces employees to change their passwords often. Also, you can ask them to use a password vault app like Last Pass to generate and autofill complex passwords. A secure password has ten characters, including numbers, symbols, and lower- and upper-case letters.
4. Enable multi-factor authentication
According to Microsoft, there is a 99% effectiveness of not getting hacked by enabling your accounts with MFA. Multi-Factor Authentication verification protects your accounts by using several authentications for even more added security by requiring multi-level verification before granting access to your account. The most common MFA that you experience is the one-time password (OTP). OTPs are those 4-8-digit codes that you often receive via email, SMS, or some mobile app. Several apps can help you with this, like Last Pass, Microsoft Authenticator, Authy, etc.
MFA Authentication examples are:
Knowledge: Password and pin and answering security questions.
Possession: OTP’s text message, software token, or hardware token.
Inherence: Biometrics like fingerprint or face recognition.
5. UPDATE Your Software!
Those update notifications can be quite annoying, but those notifications are often critical security updates in response to newly identified cybersecurity threats worldwide. It would be best if you kept all your apps and devices up to date, especially your operating system and other programs, such as Flash and Java. These security patches protect you from being breached.
6. Back up your data
Hackers and malicious threats do not only want to get your data; they also want to encrypt or erase all your data. Back it up on a secured cloud and backup your phone data.
Have you ever heard of Dropbox, Google Drive, or OneDrive? Makios Cloud Files is a bit like that but on steroids. It is designed specifically for your business, provided by a trusted source without the risk or exposure, and with all the benefits of online file storage.
7. Secure mobile devices
Security does not end at your desktop. Make a habit of safely securing your mobile device with a VPN connection while working remotely and using strong passwords and biometric features. Keep your device updated with the latest operating system. Do not save your passwords in your notes even if you have them locked; use a password vault like the one we talked about on tip number 4. Also, ensure you turn off your Bluetooth, do not automatically connect to any public Wi-Fi, and download with caution.
Protect your company
No one is exempt from a cyber-attack, but you can prevent it by training your team for the best cybersecurity practices and getting experts to help you. Remember that Cyber-attacks can happen with just one click on a corrupt link to let in a hacker into your business data. Stay ahead of cyber threats and secure your business and your employees with our managed cybersecurity services. You do not have to do it on your own; we are here to protect your business from cyber threats.
References: PR Newswire, APWG, Verizon
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.