Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
Is This a Scam? How to Identify and Avoid Online Scammers
Is This a Scam? How to Identify and Avoid Online Scammers
Are you falling victim to increasingly sophisticated online scams?
In a recent study, one in four individuals fell victim to financial scams said they fell for a scam on social media, and as we spend more and more time online, the risks of encountering a scammer are only increasing. From long-lost relatives appearing in direct messages to offers too good to be true, knowing what's legitimate and a scam can be challenging.
From phishing emails to fake websites to fraudulent online sellers, scammers have many ways to deceive internet users and steal personal information or money. However, with knowledge of common scam tactics and red flags, you can protect yourself online.
In this guide, we'll help you identify potential scams and how to arm yourself with best practices for staying safe on the internet.
Common Online Scams to Watch Out For
Scammers are getting creative – and human (as well as bot) scams operate a variety of cons tailored to take advantage of unsuspecting internet users. Knowing the most prevalent scams can help you recognize and avoid fraudulent schemes.
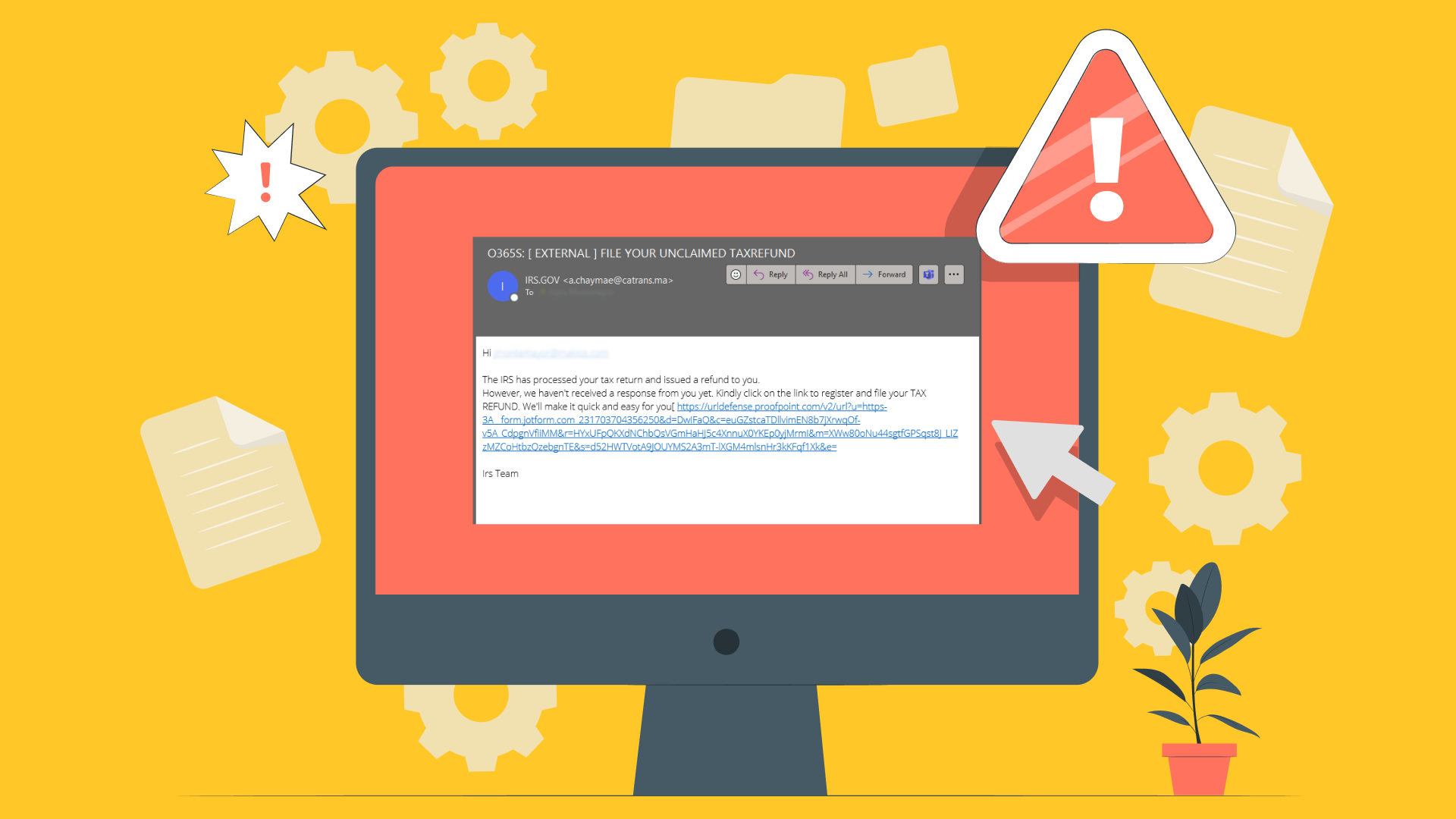
Phishing Scams
Phishing refers to fraudulent communications that appear to come from a trustworthy source, most commonly via email, text messages, or phone calls. Phishing messages are carefully designed to trick users into sharing sensitive personal information like login credentials, bank account details, social security numbers, etc.
These messages often convey a sense of urgency, demanding immediate action to verify or update an account, reset a password, or correct some system issue. Some phishing scams threaten consequences if the victim does not act quickly by providing the requested info. They take advantage of fear and limited time for reflection to exploit victims.
Phishing content may replicate company logos and messaging or spoof real email accounts. With care, scammers can make fraudulent communications appear legitimate. However, a trained eye can spot subtle inconsistencies, grammar issues, or questionable web addresses that signal a scam.
Fake Websites/Online Stores
Scammers develop online stores and e-commerce sites that mimic legitimate businesses to defraud customers. Products may be advertised at excellent prices to lure bargain hunters into placing orders—but customers soon discover they never receive the items they purchased after payment.
These fake sites are intended to collect payment details for fraudulent charges or shopping cart theft. Often, the sites have limited security protections and do not safely process sensitive financial data. Poor spelling, grammar, loose privacy policies, and dubious contact information lend clues to the illegitimacy of scam storefronts.
Users should not trust an online retailer without HTTPS browser protections for submitting payment info. Be wary of online classifieds or unfamiliar sites with hard-to-believe deals. Do your homework before providing any financial or address information.
Technical Support Scams
Technical support scams trick device users into believing something is wrong with their computer or smartphone.
Suddenly, a pop-up or call warns of a severe technical problem requiring immediate repair assistance. The scammer poses as a support rep from a trusted tech company to persuade victims into granting remote access for supposed repairs or maintenance.
Once granted access, however, the scammer can quietly install malware like keylogging software to harvest sensitive data or hold a computer ransom until extortion fees are paid. Other times, they may trick victims into subscribing to bogus support services for hundreds of dollars annually.
Legitimate technical companies do not use unsolicited pop-up messages or cold-call users with device-issue warnings or threats. Never provide credit card or login access to an unsolicited caller. Confirm a software company's technical support contacts before allowing device access.
Is This a Scam? Red Flags to Watch For
Sometimes, it's just
too good to be true. So, how do you know if a particular situation is a scam? While scammers are becoming increasingly sneaky, there are some common red flags that can point to a potential fraud:
A Sense of Urgency
Scammers try to rush targets by creating high-pressure situations that demand immediate action without allowing time for due diligence. Be wary of threats, warnings of dire consequences, or amazing opportunities with tight deadlines. Slow down and carefully evaluate the content.
Constant Requests for Sensitive Information
Legitimate businesses only ask for sensitive information like social security numbers, bank account details, or login credentials with a clear reason that you can confirm directly with the company. Object to providing this info.
Unusual Spelling and Grammar Issues
While no one is perfect, many scammer communications originate overseas. Spelling slipups, poor grammar, awkward phrasing, or overly formal language may indicate scam attempts from non-native speakers.
Inconsistent Details or Withholding Information
As scams fabricate falsehoods, suspicious inconsistencies may emerge in names, dates, and locations over time. Note the details provided and watch for contradictions.
Unsolicited Contacts
Reach out directly to an email sender or company contacting you out of the blue for verification. Many scammers pose as tech support, government agencies, or businesses to appear credible without prior contact.
Payment Demands (Even from Familiar Names)
Immediate payment demands via unusual methods like gift cards, cryptocurrencies, or third-party transfer services should raise red flags. Slow down and reconfirm payment policies with the vendor directly.
Tips to Protect Yourself from Scams
While scammers employ increasingly clever tricks, there are precautions we all must take to guard personal and financial information online:
- Never act immediately based solely on unsolicited contacts or messages. Verify legitimacy directly with the company, even if the message appears credible.
- Do not provide sensitive personal information to unverified parties. Real companies will not request things like Social Security numbers out of the blue.
- Carefully inspect URLs for misspellings or subtle differences. Many scammer sites mimic real URLs.
- Get protected online. Install comprehensive security software to block potential malware and phishing attempts via email or suspicious websites.
- Be alert to irregular payment requests like prepaid gift cards, wire transfers, or cryptocurrency. Legitimate firms generally cannot accept these.
- Do your due diligence! Search online company reviews and complaints before providing new website payment information or address details to ship purchases.
- Stay aware of unexpected "crises." Reject cold calls demanding immediate remote computer access to fix questionable issues detected. Confirm directly with software vendors.
Staying vigilant to potential warning signs of a scam and verifying requests protects from releasing sensitive information or funds to sophisticated fraudsters. Remember, if an offer appears too good to be true, it generally is.
Stay Vigilant Against Increasingly Clever Scammers
As the online world continues expanding in reach and intricacy, scammers devise increasingly persuasive schemes targeting vulnerable and trusting internet users. It may seem overwhelming to identify and combat sophisticated fraudsters who have harmfully perfected digital deception tactics.
However, there is reason for optimism. Just as technology empowers scammers, it also provides educated internet users tools to recognize and resist cunning cons. By slowing down to verify questionable requests, inspecting communications for red flags, confirming directly with companies, and monitoring accounts, individuals can employ healthy skepticism to protect identities and assets online.
Always report any suspected scams or fraud attempts to appropriate consumer protection authorities so legal action may help shut down or limit exploitative operations.
Get Help Protecting Yourself from Scammers with Makios Technology
Remember – nefarious actors constantly try to cheat others, but being forewarned and forearmed can deny them the upper hand! Want to learn more – and get expert help in avoiding scams and other forms of digital fraud? Our team at Makios Technology has the expertise and experience to help you navigate the complex world of online security.
Contact us today to learn more – and start taking steps to protect yourself online!
References: FEDERAL TRADE COMMISSION, AARP
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.