Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
Are You an Easy Target?
Are You an Easy Target?
From government agencies to international corporations and small businesses, these days it seems everyone’s data is under attack. In fact, according to the Identity Theft Resources Center, 2016 signified a high-water mark for data breaches, with 1,093 documented cases representing an increase of almost 40% over previous years. Both the healthcare industry and the small businesses sector remain an alluring target for hackers, with a total of nearly 900 incidents last year. From ransomware to phishing schemes, small business owners must maintain constant vigilance in order to ensure both the network and the data it contains remain protected from outside incursion.
Variations on a Theme
Unfortunately, protecting against data breaches and cyber attacks can be particularly tricky because hackers adapt and evolve, tailoring their actions based on the latest defenses and technological advances. Additionally, an overreliance on outdated firmware, and lapses in employee training and mobile device security protocols, allow hackers to exploit human error and network vulnerabilities.
One resource cyber criminals have in abundance is time. Hackers have infinite patience when it comes to breaching a computer’s defenses, and they have many tools at their disposal, including malware, phishing, and crypto locker viruses. By using a combination of advanced programming, social engineering, and denial-of-service (DoS) attacks, cyber criminals can endlessly chip away at a network’s security system until they find a weak spot.
While the malware category includes any software program created for malicious intent, the most common variations of malware include viruses, spyware, and bots. Viruses tend to proliferate through a computer system, causing damage as the program multiplies or initiates different executable functions designed to slow down or stall functionality. Spyware software records and stores activities that occur on your network, including URLs, passwords, and other sensitive data. Bots trigger a series of automated tasks that will repeatedly run until the bot itself is disabled.
Crypto locker viruses and ransomware fit under the malware category, but have distinguished themselves both in terms of ingenuity and impact. When a crypto locker or ransomware virus infects your system, all your data becomes encrypted and only accessible via a decryption “key” – usually available from the hacker or an affiliated provider. Ransomware attackers calibrate the monetary amounts so that the demand does not exceed a victim’s ability to pay but is still enough to cause some financial pain. Victims are provided with instructions on how to release their locked system, including directions on paying ransom via Bitcoin, and other possible actions the hackers may require. Unfortunately, many times paying the ransom will only trigger future threats, so in some cases, victims will choose to abandon the encrypted data in favor of another solution, including rebuilding a database by hand.
Once inside, cyber criminals leverage their hacking tools to encrypt data, steal sensitive information like social security numbers and banking data or disable all functions. In each instance, the motive could be anything from collecting a ransom to destroying a database or perpetrating malicious mischief. Unfortunately for the victims of a cyber attack, the reason behind the incursion matters little when critical computer infrastructure of valuable data is compromised.
It’s Coming From Inside Your Network
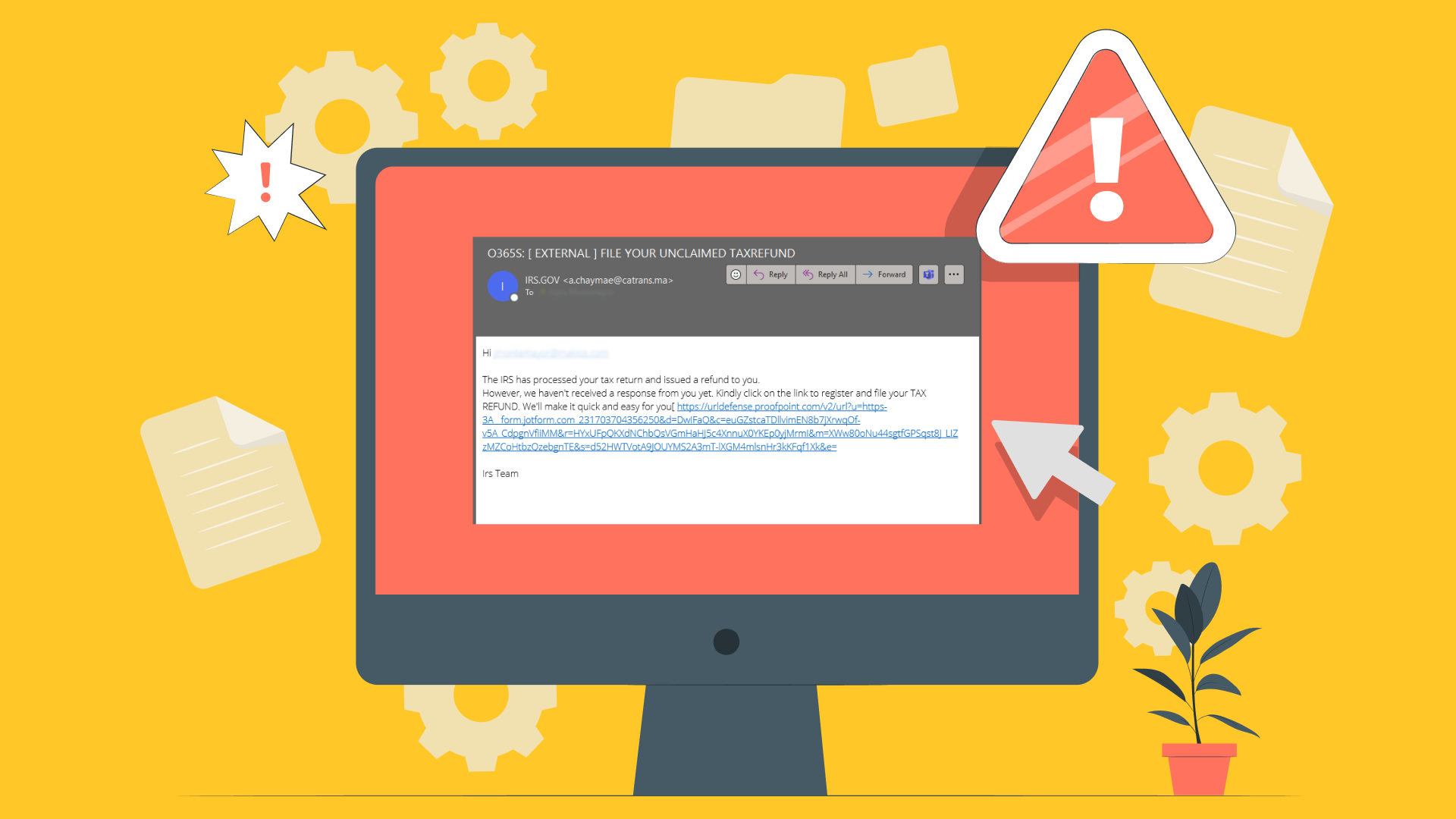
Before hackers can wreak havoc on your computer system, they must get past your security. By leveraging some basic social engineering tricks and strategies, hackers often capitalize on human nature and user error to sneak inside. With phishing, cyber criminals trick users into clicking links or opening attachments with cleverly designed emails that appeal to our natural curiosity by promising money, scandal, or entertainment. Spoofing, a variant of phishing, involves mimicking a trusted entity – like a banking institution or a known contact – to compel the click of a link or opening of a file. Finally, when all else fails, hackers can simply assume the identity of another user by cracking passwords or leveraging personal information – like birthdays and maiden names – to access the network.
Ultimately, a small business can deploy the most powerful security protocols, but if the gatekeepers can be compromised, all those defenses are useless. As a result, the best security strategy involves training and awareness. Educating employees on secure passwords and the dangers of social engineering can go a long way towards safeguarding your system. When it comes right down to it, the weakest point in your network is not your hardware or even your software; it’s the person sitting in front of the keyboard.
Don’t Go It Alone
Because the best defense involves a well-executed offense, the best way for small businesses to protect their data and devices requires implementing the kind of responsive and comprehensive security offered by a managed service provider. By partnering with a Managed Service Provider (MSP), small businesses can take advantage of the latest advances in database management, cloud storage, and network security. Operating as an extension of your internal business operations, managed IT services let you focus on optimizing your operations to boost revenue and increase productivity.
From backup and recovery services, to IT support and 24/7 help desk access, Makios MSP grants you complete operational oversight while also freeing you to grow your business, secure in the knowledge your critical operations and sensitive data are safe and secure. Tap into the power of a fully managed, multi-layer, cloud-based, monitoring and security platform that keeps your network safe and secure. Our ten layers of security give you full, real-time protection against cyber-attacks. From IPS and HIPAA compliance to PCI data loss and threat detection response, our team will detect, prevent and manage network vulnerabilities to keep your business out of harm’s way.
We all know hacking and cyber-crime continually evolves, becoming more and more complex and difficult to defend against. Unfortunately, no one technology can provide complete threat protection on its own. That’s why at Makios, deploy layered network security to stay ahead of the evolving threat landscape with a suite of powerful security services. Explore our website for more information about our comprehensive security protocols including firewall and antivirus protection, Intrusion Prevention Systems (IPS), Advanced Threat Protection, SSL/IP Sec VPN solutions, and more!
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.