Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
Dealing with Technical Problems in a Practical Way
Dealing with Technical Problems in a Practical Way
When it comes to cybersecurity, we all understand the threat, but awareness is not enough. We need to safeguard against them. But hacking concerns and computer error problems can seem overwhelming and we often ignore them. It’s human nature to procrastinate, and we know it will be expensive to have someone help with this. Every day, I help small business owners find the right security measures to fit their needs, and it all starts with a few simple steps.
Here are a few practical suggestions to start you down the path towards comprehensive and responsive cybersecurity strategy.
Start Small
Cyber security can seem overwhelming, but waiting until something goes wrong can be expensive. Start with small incremental changes. A few easy additions, like effective antivirus software and a firewall, establish a solid security foundation that you can build upon later as your needs and abilities change. In addition to initiating an antivirus protection layer, make sure to schedule regular backups of all your critical data, and keep all your software up-to-date with the latest security patches. By deciding to make an initial investment in network security for your business, you can avoid even larger bills down the line, including loss of productivity, as you pay out of pocket to rebuild your database or pay off a ransomware demand.
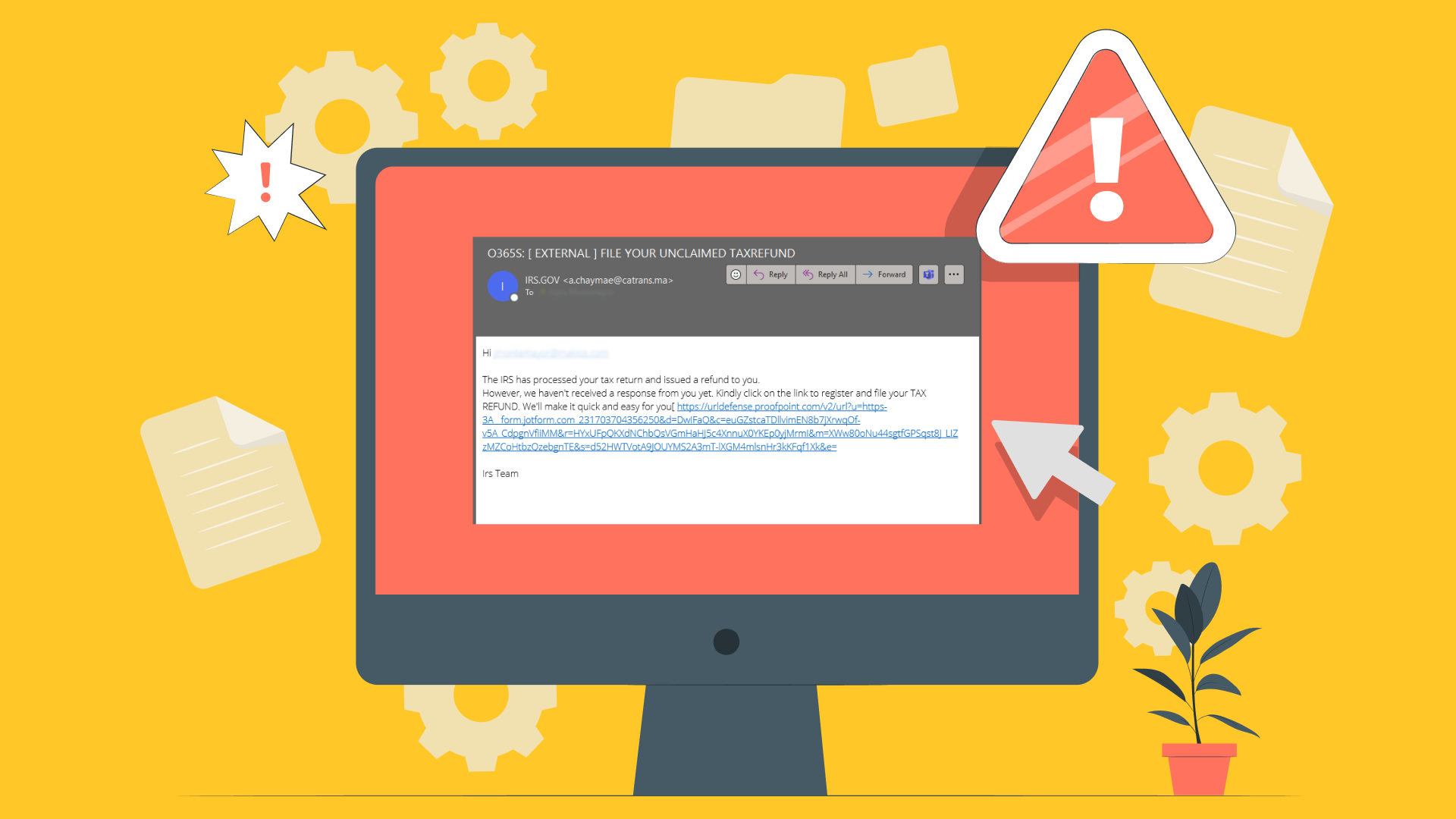
Be Aware
Information is power, and that’s never more true than when it comes to protecting your network. Make sure you and your employees are well-versed in security basics, including how to spot phishing emails and avoid clicking on suspicious links or attachments. Enforce password requirements, and monitor and manage mobile device access to your network. Cybercriminals continue to refine their attacks, and they’ve got the time to create sophisticated hacking schemes. Thankfully, many of their attempts can be stopped before they ever get into your network, as long as you and your team are aware of them and exercise caution and restraint. Make sure to schedule regular training to keep your staff up to date on your current security protocols.
Listen, we’ve all fallen victim to some online scam, clicked the wrong button or downloaded a suspicious file by mistake. Most of the time, we avoid disaster, but at a certain point that luck will run out. We can’t change human nature, but I believe we’re all smart enough to act proactively to lower the risk and avoid catastrophe. When it comes to cybersecurity, I’m my own best customer. I understand your concerns and challenges because I face them myself every day in protecting my own business. That’s why I want to make sure you have the right information to protect your network and safeguard your business.
The question isn’t what happens “if” you become a victim of a cyber attack, but rather what you will do “when” it happens. One way or another you’ll be paying me or someone like me to deal with this, so why not play defense and start working on your network security before you become a victim?
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.