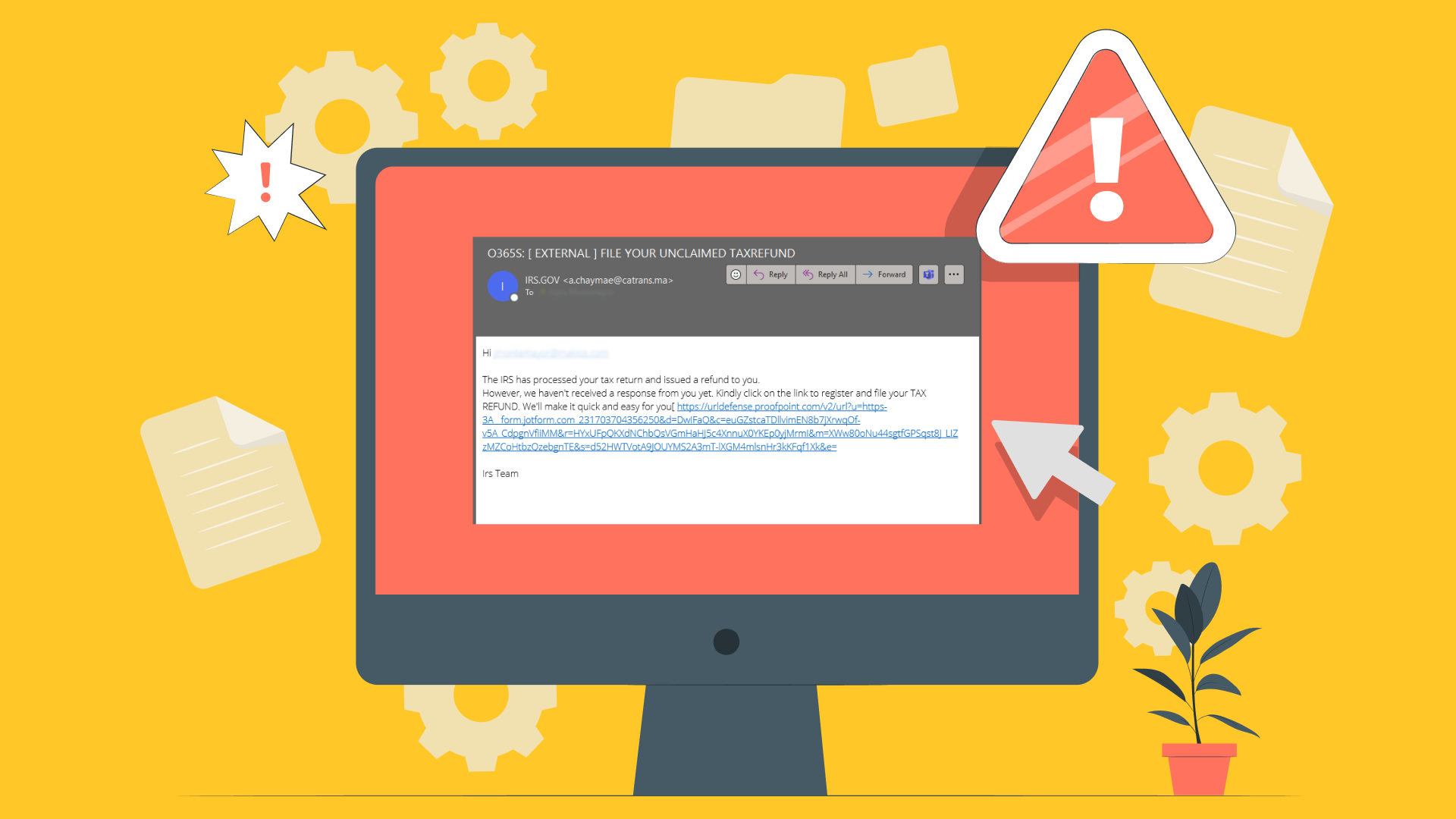
Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
Define Your Technology Risk Tolerance
Define Your Technology Risk Tolerance
Everyone has a certain level of risk tolerance. What’s yours? One way to determine the answer is to ask yourself what the cost would be if your business were disrupted or completely shut down even for a single day. Or an even more dire scenario: what if your company experienced an intellectual property data breach, or was the target of a ransomware demand? The unfortunate reality is that such occurrences could cripple your entire data infrastructure.
Companies, organizations, and entrepreneurs fall into four broad risk level categories, with risk levels decreasing as risk level numbers increase.
Level 1 – Regulatory Risk: Regulatory risk is associated with government regulations. Regulatory risk requirements will land your company in hot water with Uncle Sam. Examples of regulatory risk areas include HIPAA and wage and hour labor regulations.
Level 2 – Very Low Risk Tolerance: Companies that handle sensitive medical, financial or legal data are bound by strict regulatory requirements that demand due diligence. Companies that handle proprietary intellectual property fall into this category as well. Mistakes at this level, either inadvertent or by sabotage, expose your company to adverse legal action. Insurance may mitigate but will not eliminate possible financial repercussions, as many insurance companies have shifted a large portion of the financial burden onto their policyholders in the form of higher deductibles and copays.
Level 3 – Low Risk Tolerance: Manufacturers, service providers, retailers and similar businesses face risks from catastrophic data loss. Computer crashes, physical damage, theft or ransomware demands can put such companies in a financial – if not legal bind.
Level 4 – Moderate Risk Tolerance: Local businesses such as coffee shops or boutiques may not handle proprietary data or face federal regulatory risk, but that doesn’t mean that data protection isn’t necessary. A major data breach or long term service outage could cripple operations or shut such businesses down for good.
Rules and regulations change constantly. New threats arise nearly every day. Keeping track of these changes and emerging threats diverts energy and resources away from the core functions of your business. Data protection services can play an integral role in your company’s overall security fabric. With Makios, data protection IS one of our core functions. Let us determine your risk tolerance and devise an action plan that works for you.
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.