Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
Everything Phishing (well, almost everything you need to know)
Everything Phishing (well, almost everything you need to know)
Phishing is one of many attacks cybercriminals use to access your personal information. Once hackers get your information, they can use it to access your current accounts, steal money, and create new accounts in your name. By learning how to spot these attacks, you can stop yourself from becoming a victim of cybercriminals.
What is Phishing?
In a phishing attack, cybercriminals send fake emails to gain your trust. The emails look like they are from reputable businesses, which is why people open them. Once they have gained the victim’s trust, the cybercriminals can get the victim to reveal their passwords, account information, and other personal data.
Along with trying to get your credit card information, attackers may also use phishing attacks to install malware on your device. If you are a victim of an attack, you might not even realize it. Because these attacks seem to come from a trustworthy source, many people do not realize they’ve been compromised.
Approximately 3 out of every 4 organizations in the United States have been victimized by a phishing attack that resulted in a data breach in the last couple of years.
When phishing affects businesses, it can lead to compromised point-of-sale terminals. Attackers may even hijack your computer network until a ransom is paid. In other cases, the hackers will steal your customers’ information in order to sell it on the dark web.
This attack starts with a phishing email, call, or text. The message is carefully crafted to look like it is from someone the victim trusts. Then, the victim gives the attacker their information through a scam website or other means.
Victims are generally not targeted at random. Instead, cybercriminals will search for the kind of people they want to target. Then, they will craft a realistic-looking email, but the email will be filled with risky attachments and links.
Cybercriminals want you to click on links or go to websites without thinking logically about what you are doing. To carry out this goal, they try to stimulate your emotions instead of your rational mind. They play on fear, greed, and curiosity to get victims to open attachments.
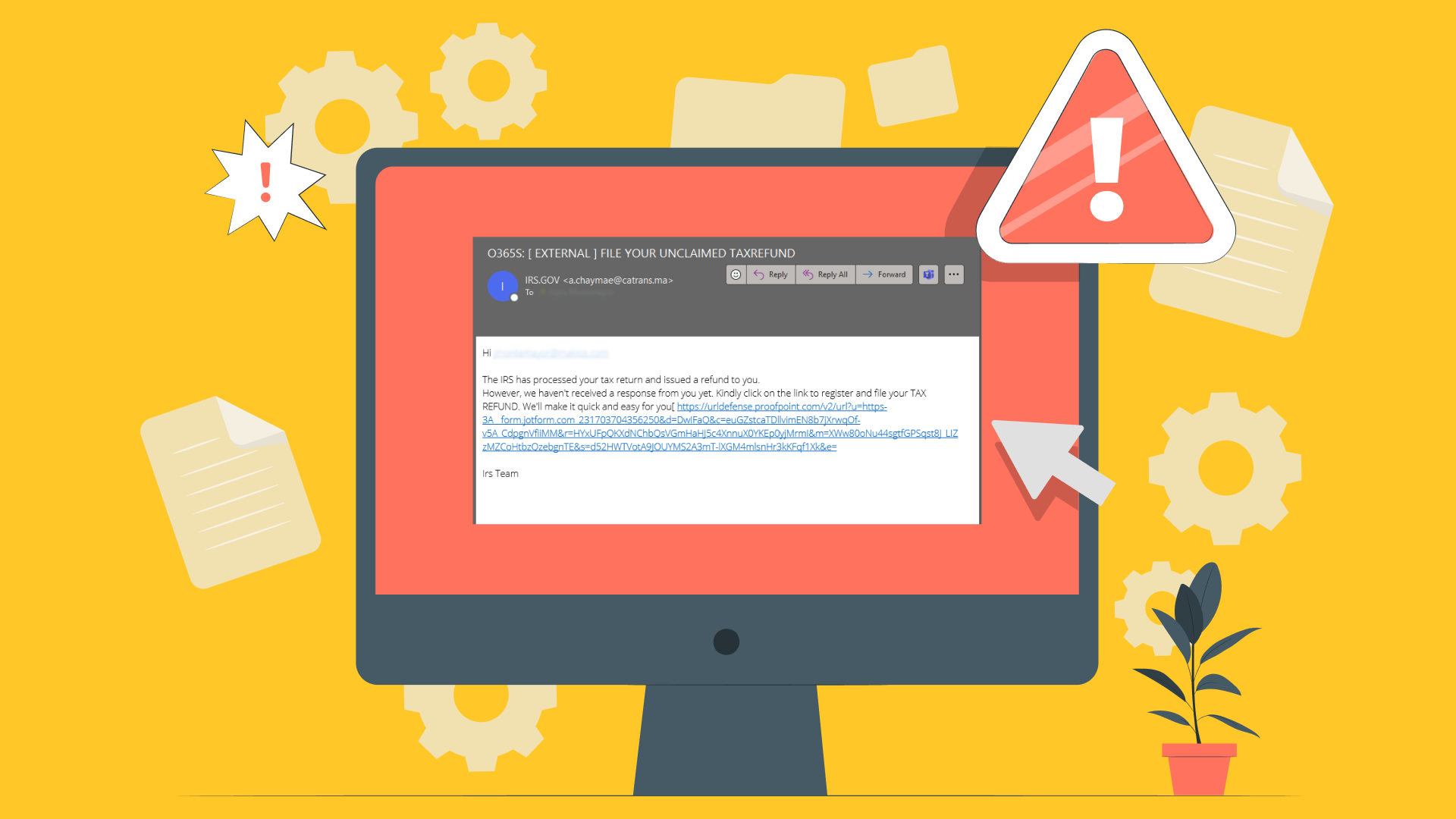
For instance, a common phishing scam involves sending fake emails from the Internal Revenue Service (IRS) about immediate due dates. The fear of an audit and sense of urgency nudge even cautious people to open dangerous attachments. Because your entire system can be compromised in a single second, it is important to always think before you click.
Types of Phishing
Unfortunately, there are many types of phishing attacks you should watch out for. From angler phishing to email phishing, these attacks can quickly lead to thousands or millions of dollars in damages if they aren’t remedied quickly.
Email Phishing
The majority of phishing attacks happen through emails. In fact, more than 3.4 billion phishing emails are sent out every day across the world.
Initially, the cybercriminal registers a domain name that is similar to a reputable company. Then, they send out thousands of emails to potential victims.
Often, the domains will look like the company's name if you are merely glancing at the email address. For example, they might turn the ‘rn’ in Thorn Company to an ‘m’ because Thorn and Thom look fairly similar. They might also turn staff@thorn.com into staff@thornsales.com because it seems like a legitimate variation.
Spear Phishing
Spear phishing involves a specific, focused attack. Instead of sending malicious emails to thousands of addresses, these emails are sent to a specific person. Often, this person is targeted because of their place of employment or job title.
In many cases, the cybercriminal already has information about the victim. Because they already know the person’s name, job title, or email address, they can create an especially realistic email.
Smishing
Smishing is when the phishing scam uses telephones instead of emails for the attack. With a smishing scam, the criminal sends a text to the victim. These texts often seem like they are from your bank, and the text will alert you to being the potential victim of a fraud.
Along with alerting you about the fake fraud, the email will give you a link to a website. Instead of helping you, the website is a fake page designed to collect your banking information.
In 2021, there were approximately
87.8 billion smishing attacks worldwide. These attacks led to over $10 billion in estimated consumer losses, which was a 58% increase from 2020.
Vishing
Like smishing,
vishing is an attack where phones are used instead of emails. Unlike smishing, vishing uses actual phone conversations. The criminal will try to get your personal information or banking details during the call by posing as an authority figure or reputable business.
Whaling
Whaling attacks are targeted attacks. Typically, they focus on senior executives at a company. While the ultimate goal remains the same, these attacks are often subtler.
Because senior executives are more familiar with phishing attacks, criminals will often pretend to be senior staff members. For example, the attacker may pretend to be a business chief executive officer (CEO) who wants a staff member to do a task. The staff member performs the favor without questioning it because they are used to following orders from their boss.
Angler Phishing
Angler phishing involves using instant messaging, social media posts, cloned sites, tweets, and fake websites to get victims to download malware or provide personal information. For example, hackers may use a victim’s public complaint on a company’s social media page to offer a fake refund. When the victim gives their card information for the refund, the scammer uses the information to steal from them.
Risks of Phishing Attacks
Phishing attacks can lead to financial and professional consequences. In addition, employees can end up giving attackers access to the company’s network and client information.
Monetary Consequences
A phishing attack can lead to devastating financial consequences. Phishing cybercriminals are stealing over $17,700 per minute across the world.
The attacker may steal money from your bank account or corporate funds. They may also run up fraudulent charges on your debit and credit cards.
Locked Files
After you are attacked, the attacker may make your work files, personal photos, videos, and other documents locked and inaccessible. In many cases, attackers will ask for a ransom fee in exchange for unlocking your files again.
Reputational Damage
If the attack affects your company, it can cause damage to your organization’s reputation.
Fake Social Media Posts and Risks to Your Loved Ones
After an attack, cybercriminals may try to impersonate you to your family members, and friends online. This can put them at risk. In addition, cybercriminals may try creating fraudulent posts on your social media accounts.
Personal Information
Attackers use phishing scams to access personal information. Other than getting your personal data, an attacker may try to get personal information from your customers, colleagues, and vendors.
What Are Common Indicators of a Phishing Attempt?
There are many common signs you should look for if you want to avoid a phishing attack. For instance, if an email asks you to download an attachment or click on a link, you should always check the email address it was sent from.
Attackers play on fear, curiosity, and greed to get victims to click on links. They also like to create a sense of urgency, so you don’t have time to think through your actions. Be wary of any email designed to invoke these types of emotions.
Before you click on a link, hover above it to see the address. If the address is written incorrectly or goes to a completely different destination, it could be a phishing attack. To avoid attacks, look for the following indicators.
- Odd or unfamiliar greetings.
- Attempts to create a sense of urgency, like saying immediate action is required.
- Domain names and email addresses that don’t match.
- Misspellings, typos, and grammar errors.
- Requests to transfer funds or provide your login details.
- The offer is too good to be true.
How to Protect Against Phishing Attacks
Fortunately, you don’t have to become a victim of a phishing attack. There are a few things you can do to stop these attackers from accessing your important information.
Educate Your Team
While they might not mean to, your employees pose the biggest risk for your business. Phishing attacks rely on human error, so you need to train your team about phishing attacks, what to watch out for, and how to deal with potential attacks.
Use Multi-Factor Authentication
Multi-factor authentication is when a program relies on more than a single password to give you access. For example, many financial websites also require you to input a special code from a text after your initial log-on. By using multiple log-in steps, this technique can prevent attackers from successfully gaining access to your accounts.
Keep Your Devices Updated
Your device needs to be updated with new security patches. Otherwise, attackers can use known vulnerabilities to access your device.
Do Regular Data Backups
If there is a problem with your device, you may need to return to a previous backup. Ideally, your data should be stored off-site and off of your company’s network, so it will remain safe if your company’s network becomes compromised.
Integrate Security Software
The right security software can prevent you from becoming a victim. A good security system can spot malicious attachments and links, so you don’t have to worry as much.
Get Email Protection
You can reduce your chances of becoming a victim by investing in email protection, like
Makios Cloud Email Protection. It serves as a filter between the sender and you, so you don’t receive malicious links, junk mail, or spam.
Report Phishing Threats
If you receive a suspicious email, don’t open it. Instead, report it to your IT department, so they can alert other people to the potential threat. You should never assume someone else has already reported an attack.
Protect Yourself From Cybercriminals
Whether you are running a multi-national business or just want to receive birthday messages, you have to be careful about the things you send and receive. Through email protection and other cybersecurity services, you can keep your business and personal information safe.
To learn more, reach out to Makios today!
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.