Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
Get the Insights You Need to Make Your Tech Decisions
Get the Insights You Need to Make Your Tech Decisions
1. Physical
Technology you see and touch.
When assessing the physical components of your network, we should look at all hardware to develop a better understanding of the types of computers you are using and how those systems have been maintained. It is important to check for warranties and substandard repair work.
Sometimes the aesthetics alone tell the story: messy wires and dusty machines tucked in a corner can indicate a system that’s ripe for failure and full of potential problems. Because older machines eventually run software too old to be updated, we keep an eye out for outdated operating systems capable of compromising your entire network.
2. Logical
How it's all configured.
Once we gain a clear understanding of your hardware resources, we move on to the logical component of your system by determining how well it performs based on standard expectations.
We check HCP configurations and analyze your DNS and IP schemes. We chart your active directory organization, account setup, and other internal policies. The insight gained from the logical layer analysis helps us establish a framework where we can test for network vulnerabilities and build a foundation for better protocols.
3. Security
Securing your technology.
While we assess the status of the physical, logical, and communication side of your business operations, specific security measures must also be evaluated. We check for antivirus and spam protection and determine if anything more than the very basic security protocols are being used. Because of our network security expertise, we bring a level of knowledge and experience above and beyond the standard.
Firewalls and virus scans are always a good start, but advances in technology now provide a whole arsenal of security tools, including Unified Threat Management (UTM), intrusion prevention, data loss prevention, and Advanced Persistent Threat (APT).
We also understand the importance of cryptolocker, Reputation Defense, and next generation firewalls and antivirus software. Our 15 layers of network security create a sophisticated and responsive shield able to continually adjust to new threats while always providing superior network protection.
4. Communication
How you communicate.
Because many network security issues begin at the user level, establishing the way information travels through your system, including user access, lays the groundwork for creating defensive strategies to eliminate the risk of cyber-attacks or other cyber crimes.
Determining the status of your communications component involves evaluating current email, internet, and telephony providers, along with any cloud services currently utilized, like iCloud or Dropbox.
5. Strategy
Bring it all home.
We conclude our ITR with the strategy component. We evaluate your business practices and strategy. We take a look at your business plan and processes, your budget, and your plans for growth. We analyze whether those are in alignment with the current and future needs of both your business and your employees.
Our knowledge and experience allow us to provide solutions aimed at saving money and improving efficiency over the life of your business, rather than a cheap fix that will only trigger more issues down the line. And because we develop an understanding of how your business operates, we can pinpoint areas of redundancy and help create an atmosphere that promotes productivity and informed business decisions.
After a complete evaluation of each component, we present you with your results and our recommendations which include a score rating the effectiveness of your current setup as well as potential areas of improvement.
The next step is to decide if Makios is a good fit for you.
After the 10,000-foot view of the preliminary ITR, true onboarding begins. All the elements from the first survey will now be broken down into individual details with an eye towards increasing operational efficiency while maintaining top-notch security and data reliability.
You are assigned a virtual network engineer (VNE) who will be with you for the duration of your contract. The VNE works with you and your employees to ensure that all of your systems are monitored and up to date and tweaks are made when necessary. We work with you on strategy and planning so we can implement and roll out new systems and software to help your business become more productive and continue to grow.
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
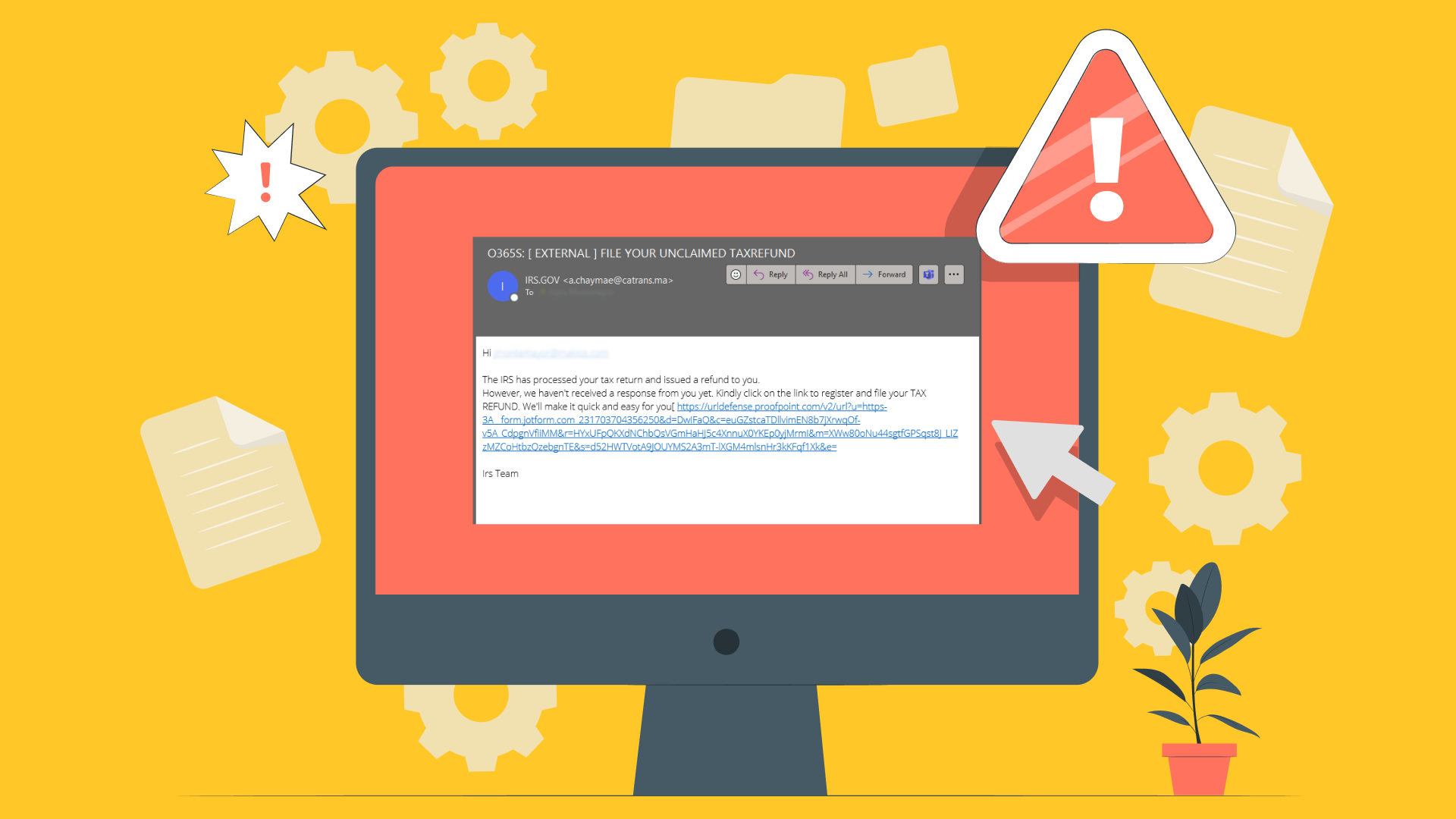
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.