Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
Types of Hackers: Who Are They and What Do They Want?
Types of Hackers: Who Are They and What Do They Want?
When people hear the word “hacker,” most of them think about a person sitting in their basement, trying to steal information away from businesses for their profit or to cause harm. This stereotype was partly overblown by the mainstream media, but it also has a level of truth to it.
Not all hackers are evil, though. There are ethical hackers, or white hat hackers, who do this to help individuals and companies be more secure online. There’s also a gray area, where hackers do this partly for their entertainment and partly for profit. We are going to explain what a hacker is and the types of hackers.
What is a Hacker?
A hacker is a highly-skilled computer programmer who uses their knowledge and skills to bypass a computer’s security system as a means to access private information and data and achieve their goals.
There are two official definitions of hackers in the dictionary:
- an expert at programming and solving problems with a computer
- a person who illegally gains access to and sometimes tampers with information in a computer system
Hackers typically have exceptional programming skills and computer knowledge, although that’s not necessarily required. They know how to bypass a computer’s security system and access data and information that they wouldn’t have been able to get otherwise (as well as data that’s not available to the public).
Having these details gives them leverage to do whatever they want with this information. In some cases, hackers turn out to be malicious as they will demand something in return for what has been taken. Their sole goal is to harm a person or a business with their actions. Unfortunately, this type of hackers is the most prevalent type you’ll find across the world.
In other cases, hackers do this for their pleasure or even help others improve their security and identify leaks in their security system. The latter are called “white hat” hackers or ethical hackers. This term has been coined to distinguish good hackers from the bad.
Depending on their end goal, there are various types of hackers you should know of.
Types of Hackers
In general, we can split hackers into three main categories:
- White hat hackers (the “good” hackers)
- Gray hat hackers (hackers who do this for pleasure and minimal personal gain)
- Black hat hackers (malicious hackers)
How do you distinguish each type of hacker, and what are their primary motivations?

White Hat Hackers
White hat hackers are often employees for businesses, large corporations, and even government entities. They look to find gaps and vulnerabilities in their company’s security systems. They are the desired type of hackers companies employ to help them improve their cybersecurity management.
These hackers are also called ethical hackers. They need to have the same prowess and skill level as hackers looking to cause harm to find gaps. Because of this, they utilize mostly the same methods as black hat hackers.
They do monitoring tests to identify weak areas in security systems. They will help strengthen a company’s security system to help them protect themselves from black hat hackers.
The main goals of white hat hackers include:
- A desire to help businesses and companies improve their security.
- Looking for gaps and holes in the security systems of these companies.
- Putting protective measures in place to protect companies from gray and black hat hackers.
The difference between white hat and black hat hackers is ethical hackers have permission from the security system’s owner to access the system and repair it. On the other hand, black hat hackers do it without this permission, making their actions illegal.

Gray Hat Hackers
The second type of hacker is caught somewhere between white hat and black hat hackers, thus the fitting name. Gray hat hackers typically have the same knowledge and skills as white and black hat hackers.
However, their goals will vary. Most gray hat hackers simply do this for their own pleasure. They want to test their skills and prove to themselves they are good at it. Most of the time, they will do it without the owner’s permission, although their goals are generally not to harm the other person.
This makes them a mixture of white and black hat hackers. Some gray hat hackers want to get compensation for their services or seek payment from the owner for exploiting the flaws in their system. They’ll report any sort of findings to the owner, but they’ll (most often) not try to use them for their gain.
The goals and motivations of gray hat hackers include:
- Exploiting gaps and holes in security systems and presenting them to their owners.
- They don’t usually care about stealing from people and are not malicious on their own.
- They might sometimes require payment for what they’ve discovered from the security system owner.
- Generally, gray hat hackers do this for fun.
These types of hackers are prevalent in their own way. They are different from white hat hackers because they don’t have permission from the owner to make these changes. They’re also different from black hat hackers in the sense that they’re rarely harmful.

Black Hat Hackers
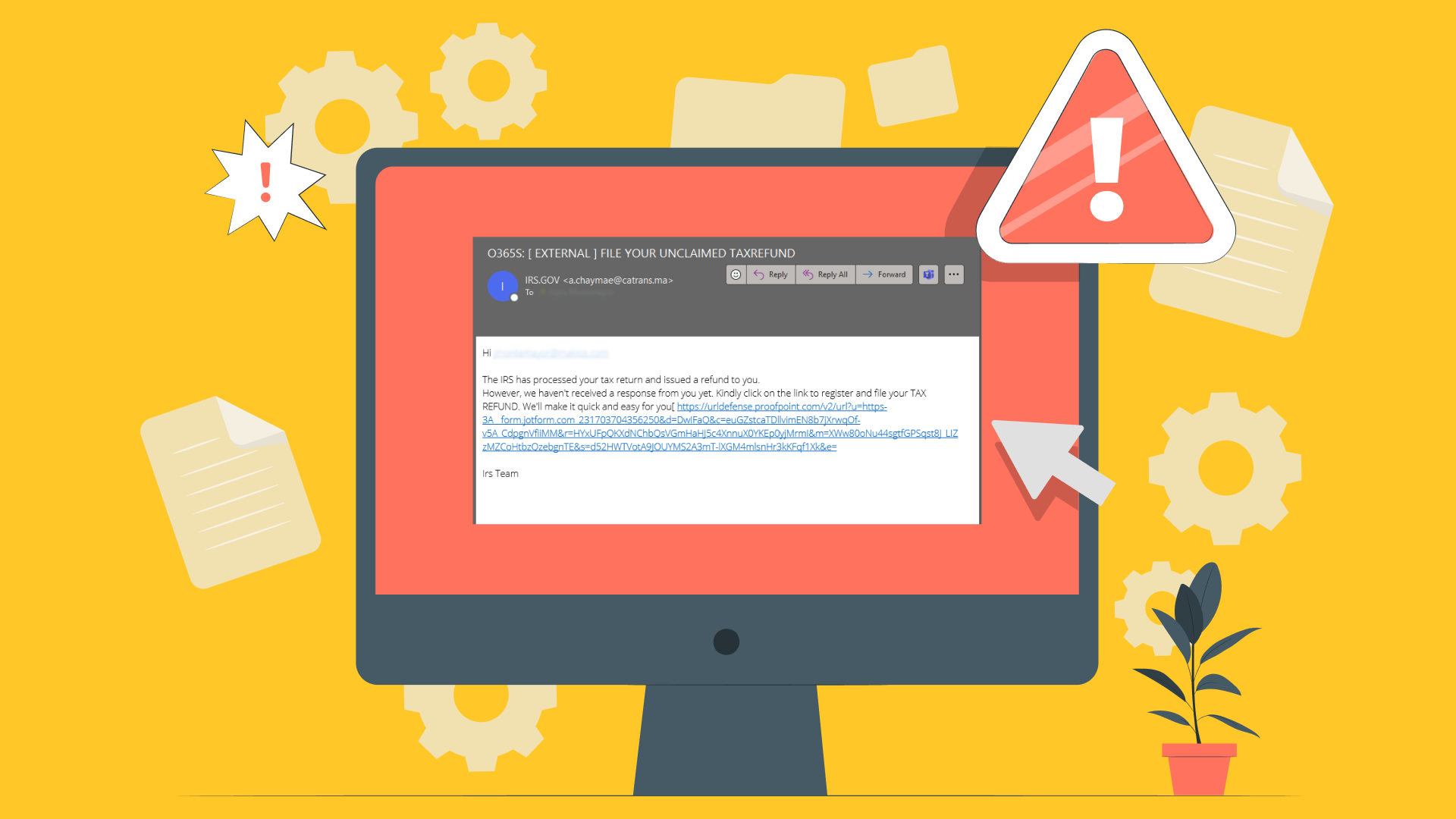
You have likely read about cybercriminals trying to access your data and information illegally. That’s what black hat hackers do. They create malware, which are programs that infiltrate your security system and gather private information and files, such as bank details, confidential data, login credentials, and more.
They do this for four main reasons:
- To earn money from what they do as they sell this information on the black market.
- To exploit the system and get sensitive information to bully people into paying them money.
- To steal money from their victims using confidential data.
- Simply to cause harm to the “recipient” of their hacking.
Some “unethical hackers” are highly skilled in what they do, but these people will typically not target random individuals. They will set their sites on large companies or do it for political reasons, or even for protesting means.
On the other hand, some amateur black hat hackers (the prevalent type on the internet nowadays) try to infiltrate your security system to get information from you for their gain. This type of hacking is illegal, and the hackers never have the permission of the owner.
The bad thing is that there are many hackers of this type accessing information all over the world. The good news is that you can stop them effectively with a few preventative measures.
How to Protect Myself from Hackers
What can you do to stop hackers from stealing from you? Follow these tips, and you’ll be well-protected from the perils of internet bullies.
1. Use Managed Cybersecurity Services
Managed Cybersecurity Services are provided by companies like Makios Technology that will help you strengthen your information security system.
Finding a reliable managed cybersecurity service provider will help you detect and prevent threats, reduce vulnerability to hackers, protect your identity and information online, and find gaps in your security system.
This solution is a viable and cost-effective solution for individuals but mainly for companies that don’t have the knowledge needed to stay safe online or businesses that don’t have their cybersecurity specialists.
2. Use an Efficient Antivirus Program
Good antivirus software will not always be the most effective solution for staying safe online but it will help you put some useful preventative measures in place. It will help you detect threats that are potentially harmful to your computer and eliminate them. Antivirus software can also find malware that poses as standard files you download on the internet, which can exploit your system to find data and information you don’t want to give away.
3. Be Careful When Using Public WiFi
When you use public WiFi connections, your data and information are vulnerable to hackers using the same network. That’s why you should never use your bank details or enter passwords when you use public WiFi at local libraries, Starbucks, and other places that offer it for free. Usually, the security of these open WiFi connections is not as tight as your connection at home. It’s good to be aware of this when you use a public network.
4. Use Software to Run Tests Regularly
You can also run security tests continuously yourself. You will need some basic skills and knowledge for this, though some programs will do this automatically. You can use antivirus software for this but there are dedicated penetration testers available as well.
5. Only Download from Sources You Trust
This is an essential tip for staying safe from hackers – don’t ever download files from unknown or questionable sources. If a website appears sketchy and doesn’t have a known reputation for being a safe source, it may not be a good idea to use their service.
Ensure You Are Protected from Hackers
Hackers are people with good computer and programming skills that find gaps in networks to access private information and files. Some hackers are “good” hackers, while others want to do harm.
Protecting yourself from black hat hackers is crucial to keeping your files and other information safe. Professional quality managed cybersecurity services from Makios Technology will do a lot of good for your security online.
Learn more about how we can keep you protected. Give us a call today at (915) 217-2500 or take a moment to complete our online contact form.
References: Merriam-Webster
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.