Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
What Is Spoofing?
What Is Spoofing?
Is your system at risk of being compromised by a spoofing attack?
Spend enough time online, and you'll soon realize that risks to your data and security lurk around every corner. From phishing scams to malware, scammers always look to take advantage of unsuspecting users.
These threats can be catastrophic for businesses that depend on networks and the web to function. One technique that cybercriminals use to breach a network's security is called spoofing.
Spoofing – the act of impersonating a legitimate source – is an increasingly common attack vector. In this tactic, hackers disguise themselves as a trusted entity to gain access to sensitive information or control over a system. Similar to phishing, spoofing relies on social engineering tactics to trick users into providing sensitive information or granting access.
The risks of spoofing are enormous. Studies show that in 2022 alone, over 300,000 unique networks fell victim to spoofing and phishing victims, with a financial loss of $52 million in the US alone.
So, what's the best defense against spoofing? Educating yourself and your employees on spotting and preventing these attacks is crucial.
What Is Spoofing?
Spoofing, at its core, involves disguising the source of online communications or data. The aim is to appear to be a trustworthy or authorized entity to manipulate the receiver into providing sensitive information, enabling cybercrimes.
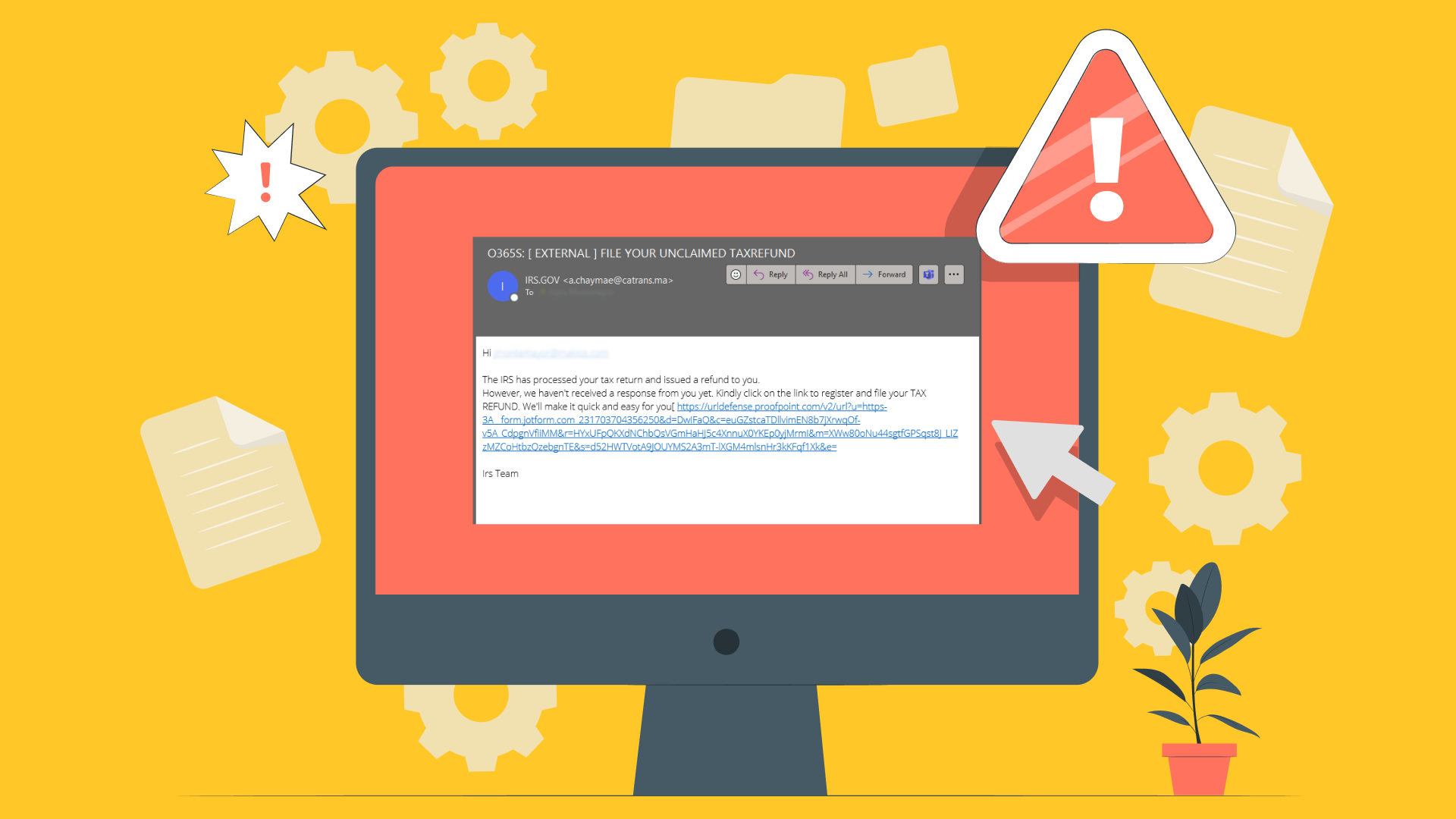
For example, email spoofing is a common method where a cybercriminal fakes the sender's address in an email. This allows them to impersonate a trusted contact, company, or organization by making their message seem to originate from a legitimate email address. Spoofed emails often enable phishing scams or spread malware.
Other ways spoofing might manifest:
Website spoofing: Creating fake websites designed to mimic real sites in order to capture entered data like usernames and passwords. This is done by using similar URLs and webpage design.
Caller ID spoofing: involves falsifying the phone number displayed as the caller ID to disguise the actual originating number. This allows scammers to appear to be calling from a trusted entity, such as a government agency or well-known company.
GPS spoofing: Transmitting false GPS signals to make a GPS receiver calculate an incorrect location. This can enable the hacking of autonomous vehicles, drones, and more.
While these examples require technical sophistication, user awareness, and safe online practices remain the best defenses. Educating employees, implementing cybersecurity policies, and utilizing available protections go a long way toward prevention.
Individuals and organizations can identify and guard against spoofing threats with a proper understanding of the risks.
Recognizing Spoofing Attacks
Spotting spoofing attempts requires knowledge of common red flags:
- Urgency or pressure to act quickly: Scammers often use high-pressure tactics to short-circuit critical thinking, so targets act on impulse or fear rather than logic. Requests that convey dire urgency should raise suspicion.
- Unexpected requests for sensitive data: Reputable organizations rarely contact you unexpectedly, seeking private details like passwords or financial information. Out-of-the-blue data requests should prompt scrutiny.
- Unusual points of origin: Carefully check the source of questionable communications claiming to be from trusted entities. For example, verify email addresses or check caller ID area codes against actual business locations.
- Poor grammar/spelling: While not foolproof, lousy grammar or misspellings can signal untrustworthy communications from some fraudsters. Well-crafted messages suggest more authoritative sources.
- Suspicious links/attachments: Links or files from unknown contacts carry inherent risks. Never provide data to unfamiliar sites or enable attachments before vetting.
Naturally, advanced spoofing attacks can avoid the most common red flags and deliver convincing messages, so don't solely rely on these tactics. A proactive defense that prevents email security compromises and blocks malicious traffic is still essential.
Tips for Avoiding Spoofing Attempts
Ensuring your system is safe from spoofing attempts is crucial for protecting sensitive information and maintaining customer trust. Here are some tips to help you identify and avoid spoofing attempts:
Implement Security Protocols Proactively
The most effective spoofing prevention relies on technological protocols before incidents occur.
At a minimum:
- Install comprehensive antivirus/antimalware applications to detect spoofing attempts and block threats automatically through email, web traffic, and endpoints.
- Utilize firewalls and enhanced network security monitoring to identify suspicious traffic and block known malicious IP addresses.
- Enable spam filtering on networks and inboxes, keeping them updated to catch new spoofing tactics. Quarantining questionable emails limits user exposure.
- For websites, obtain trusted TLS/SSL certificates to enable encryption and validate authenticity through issuer confirmations.
Strengthen Human Defenses
Well-trained and security-conscious employees provide indispensable protection:
- Inform all employees on fundamental spoofing detection methods through ongoing simulated phishing tests. Ensure recognition capability across the organization.
- Implement strong password policies plus mandatory multi-factor authentication for remote access and admin accounts to prevent unauthorized access through stolen credentials.
- Establish data and network access hierarchy with need-to-know permission tiers to limit spoofing risks should a breach occur. Compartmentalize sensitive materials.
Respond Swiftly to Suspected Incidents
Reactivity after suspected spoofing also reduces exploitation:
- Report all potential spoofing attempts according to established channels, detailing specific suspicions. Emphasize urgency and need for investigation/response.
- Immediately isolate any suspect messages, links, or suspicious endpoints from wider access until forensic analysis, limiting wider organizational exposure.
- If spoofing confirmed, do a full audit of systems accessed from compromised accounts or endpoints. Reset ALL related access credentials regardless of confirmation.
With technological barriers augmented by sharp employees through robust cybersecurity policies, organizations drastically reduce risks from spoofing and related attacks. Ongoing training and protocol updates provide flexible defense as threats evolve.
What Is The Difference Between Phishing and Spoofing?
It's easy to confuse phishing and spoofing, as they are both tactics used by hackers to gain access to sensitive information. However, there is a key difference between the two.
Phishing is the act of sending fraudulent emails or text messages that appear to be from a legitimate source to trick individuals into providing personal information such as usernames, passwords, or credit card numbers. These emails often contain urgent or alarming language, creating a sense of urgency for the recipient to take immediate action.
On the other hand, spoofing involves impersonating a trusted entity's email address or website to deceive recipients into believing that the communication comes from a genuine source. This can include using similar domain names or altering display names to make it seem like the email comes from a legitimate source.
Both phishing and spoofing are commonly used tactics by cyber criminals to steal sensitive information and gain unauthorized access to personal accounts. They can also be used to distribute malware or ransomware, which can cause significant damage to individuals and organizations alike.
Stay Vigilant Against Constantly Evolving Threats
No prevention regime is flawless, but companies who systematically inform employees on spotting threats ensure an extra layer of human defense to complement technical tools. Swift and decisive response protocols for confirmed or suspected incidents also reduces exploitation.
For any suspected spoofing attempts or related cybersecurity concerns,
contact us to learn how you can better protect yourself and your organization. Remember, the best defense is a proactive offense.
References: Forbes
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.