Portals El Paso, TX (915) 217-2500 | Grapevine, TX (817) 752-9400
What is Email Security? Most Common Attacks, Tips, & More
What is Email Security? Most Common Attacks, Tips, & More
Email has long played a central role in how we communicate. From business deals and catching up with old friends to receiving updates from our favorite brands, it's a tool billions of people use daily.
How many times have you checked your Gmail, Yahoo, or Outlook today? With its vast reach, the importance of maintaining email security cannot be stressed enough.
What is Email Security?
At its core, email security refers to the various techniques used to keep sensitive information in an email communication safe from unauthorized access, loss, or compromise.
Imagine your email as a postcard. If not properly secured, anyone could read, alter, or misuse the information on that postcard. With the rise of cyber threats, the data and personal information at risk in our emails are even greater.
It's not just about keeping messages private. It's about protecting our financial details, personal photographs, business contracts, and so much more. Email security ensures that our digital conversations remain private and that only the right people access the information.
Email protection tools like email filters and Secure Email Gateways (SEGs) are just a few ways to ensure this security. As we dive deeper, we'll explore more about these tools and the common threats we face in the digital age.
Most Common Email Attacks
Every day, countless emails zoom across the internet. While many are harmless, others hide dangerous intentions. Let's take a peek into the world of malicious emails and get to know the usual suspects.
Phishing
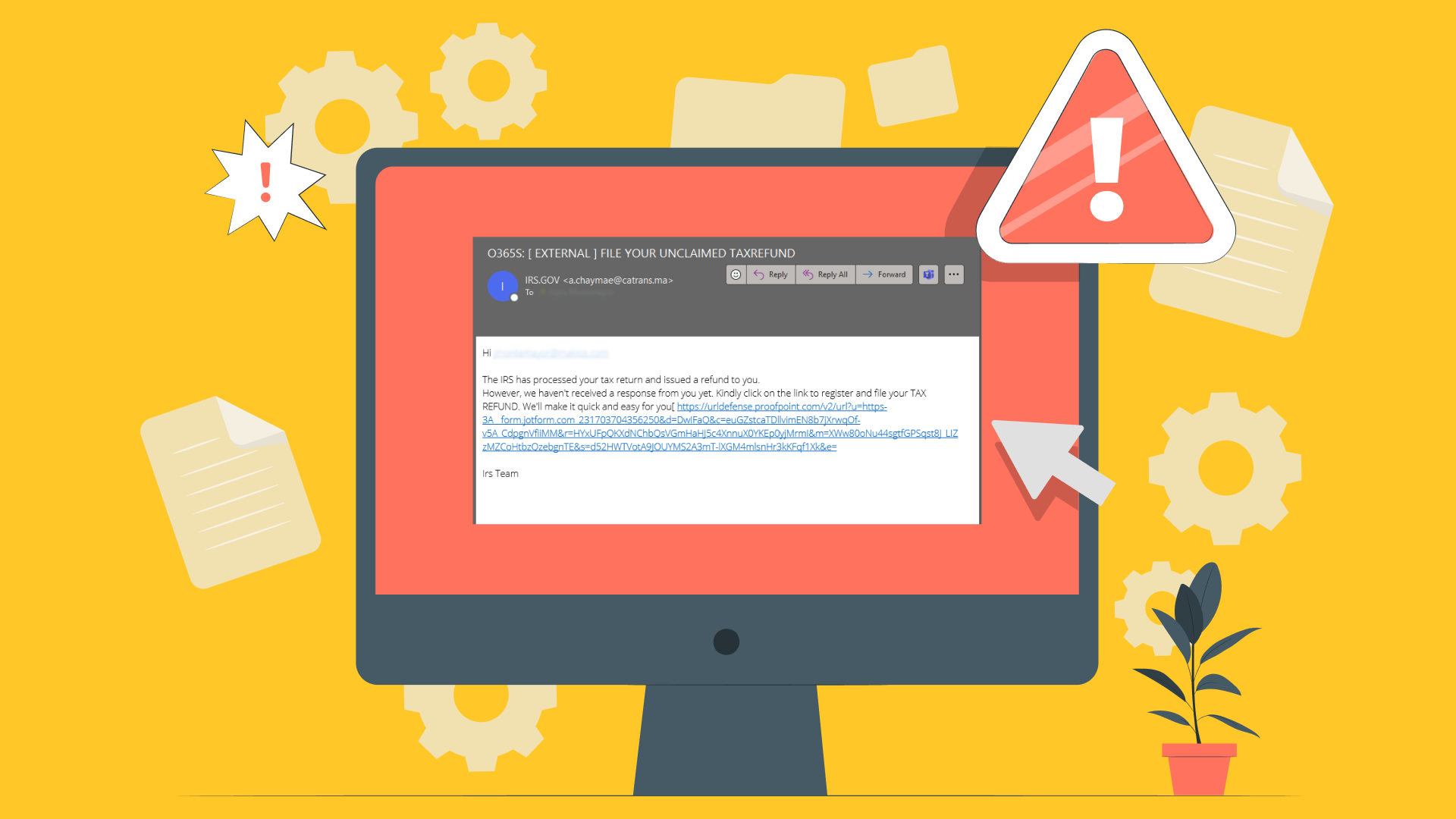
Picture this: an email that looks just like it's from your bank, asking you to "verify" your account details. While this may seem harmless, this is a common type of phishing email that millions of people receive every day.
Phishing emails are clever fakes, trying to trick you into handing over personal info. They portray themselves as a brand you trust and steal the details that you’d normally be willing to give the real organization.
Spear Phishing
Think of this as phishing's sneakier cousin. Spear phishing emails are custom-crafted to target you specifically. Maybe it's using your name or referencing a project you're working on.
The goal is to make you drop your guard and share sensitive details. Hackers and email scammers often do research on individuals before sending these emails, making it easier for them to appear legitimate.
Malware and Ransomware Attacks
Ever get an email with a strange attachment? It’s never a good idea to open these from someone you don’t know or aren’t expecting messages from.
Some of these carry harmful software called malware or ransomware. Open malware and you might let in a digital burglar that can hijack your information. Ransomware goes a step further, locking your files and demanding money to release them.
Man-in-the-Middle Attacks
Imagine sending a letter but someone intercepts it, reads it, then reseals it and sends it on its way.
In the email world, this interceptor is the "man in the middle", sneaking a peek and maybe even altering your messages.
Domain Spoofing
You get an email from a trusted company. But something's off. Domain spoofers use fake domains that look like trusted ones.
Instead of Gmail or Yahoo, it might be "Gmall" or "Yohoo". They're banking on you not noticing.
Spam and Junk Mail
Overflowing inboxes with offers, deals, and more. That’s what we’ve come to expect from spam and junk mail.
Annoying? Yes. Harmful? Sometimes, if you’re not careful.
Buried in those offers might be risks like bad links, viruses, and beyond. Always be cautious.
How to Recognize Suspicious Emails
Navigating the vast digital landscape of emails can sometimes feel like tiptoeing through a minefield. While many messages are genuine and safe, some carry hidden threats.
How can you tell which emails to trust and which to toss? Let's talk about the tell-tale signs of a suspicious email.
Check the Sender's Address
Genuine emails, especially from established organizations like Gmail, Yahoo, or Outlook, will usually have an official domain. Be wary of slight misspellings, such as "support@gmall.com" instead of "support@gmail.com". Such tricks are common tactics employed by scammers.
Unexpected Attachments
Did you receive an email with an attachment you weren't expecting, especially from an unfamiliar sender? This is a big red flag. Malicious software can easily hide within seemingly harmless files or links.
Urgency and Threats
Beware of emails that create a sense of urgency. Phrases like "Your account will be suspended" or "Immediate action required" are often used to rush you into making a mistake.
Grammatical Errors
Many phishing emails originate from non-English speaking countries. Look out for awkward phrasing, spelling mistakes, or odd formatting.
Too Good to Be True
Those emails that offer spectacular deals, big lottery wins, or unbelievable offers? If it seems too good to be true, it probably is.
Requests for Personal Information
Legitimate organizations will never ask for sensitive information like passwords, Social Security numbers, or bank details via email.
Check the Links
Hover over any links (but don’t click!) to see where they lead. A long, jumbled string of characters or a misspelled version of a known website are signs of a scam.
Generic Greetings
If the email starts with "Dear User", "Dear [Your Email Address]", or “Hello Dear”, be cautious. Genuine emails from companies you do business with will typically use your name.
Verify Independently
If you’re ever in doubt about an email's authenticity, reach out to the company or individual directly using contact information obtained from their official website or other reliable sources. Don’t use the contact details provided in the suspicious email.
A little skepticism goes a long way when it comes to email security. Adopting a cautious approach and learning to spot these signs will greatly reduce the risks of falling victim to email scams. Always remember trust but verify.
Tips for Enhancing Email Security
Regularly Update and Patch Software
Just like your phone gets updates, your email software needs them too. Whether you use Gmail, Yahoo, or Outlook, it's key to keeping them up-to-date. Each update might fix security holes that hackers can exploit.
Use Strong, Unique Passwords
Think of passwords as keys. You wouldn't use a flimsy generic key for your house, right? The same goes for email.
Create passwords that are a mix of letters, numbers, and symbols. And remember, no "password123". It’s also a good idea to avoid using the same password across multiple sites. This way, if one gets compromised, the others remain safe.
Two-Factor Authentication (2FA)
Imagine a second door behind your main door. That’s 2FA for your email.
Even if someone guesses your password, they'll need another code (usually sent to your phone) to get in. It's like having a double lock.
Be Wary of Unsolicited Attachments
They say curiosity killed the cat. Don’t let it harm your computer.
If an email from an unfamiliar sender has an attachment, think twice about opening it. The document or file might contain something harmful. If you didn't expect it, better to leave it unopened.
Educate and Train
Knowledge is power. Everyone using email, from kids to grandparents, should know the basics of email security. Talk to your family. If you’re a business leader, consider training for your team. It takes only one click on a bad link to open the door to problems.
The Role of Email Security Solutions
Email is one of the primary doors through which both welcome guests and unwanted intruders can enter. Luckily, there are specially designed tools and solutions to help guard that entrance.
Just like smartphones have apps and features, firewalls come with their own set of special functions.
Advanced Filtering
Picture a diligent postman. He knows every member of your household and hand-delivers only the mail that belongs to you, while keeping out junk mail and suspicious packages.
Advanced email filtering acts in much the same way for our email. It sorts through countless messages, ensuring we get what we need while blocking unwanted and harmful emails.
Encryption
Have you ever used a secret code to share messages with friends? Encryption is like that, but way more complex.
When you send an email, encryption turns your message into a secret code. Only the person you're sending it to has the special key to decode and read it. This means that even if sneaky eavesdroppers intercept your message, all they'll see is gibberish.
Regular Backups
Remember when we used to keep photo albums and important papers in safe boxes? Now, much of our precious data is digital. Just like those old boxes kept our memories safe, regular backups protect our digital treasures.
By regularly saving copies of our emails, we ensure that even if something goes wrong – say, an accidental delete or a nasty virus – we can recover what's lost.
While we adore the convenience emails bring, they also come with their set of challenges. But with the right email security tools by our side, we can navigate the email world with confidence.
Need Reliable Email Security?
You might be wondering whether your email security is up-to-date and how you can keep up with this need. That's where experts like Makios Technology and services like our Makios Cloud Email Protection come in.
We have all the tools you need to keep your email communications safe and protected. Please
get in touch with our team today so we can provide you with the top email security options!
You may also like
Have more questions or need further assistance? Let us know how we can help you with the unique needs of your business. Get in touch online or call us today at (915) 217-2500!
Cybersecurity for Businesses
Services
Management
Consulting
Cyber Security
Email Services
Cloud Internet
VoIP & Internet
Microsoft 365
Hardware & Software
Finance & Leasing
Websites & SEO
Industries
Healthcare
Engineering
Transportation
Construction
Insurance
Legal
Financial
Real Estate
Logistics
Manufacturing
About
Newsletters
Stewardship
Partners
News
Certifications
People
Employment
History
Clients
Company
Copyright © 2006-2023 All Rights Reserved. MAKIOS® is a registered trademark of Makios Group LLC, a Texas Company.